Locked Out After Third Attempt
Manage unsuccessful login attempts with account lockout policy
Larn how to create account lockout policies that particular how many unsuccessful login attempts are allowed earlier a countersign lockout in guild to prevent credential-based attacks.
Due to the often overwhelming prevalence of password hallmark, many users forget their credentials, triggering an account lockout following too many failed login attempts. Upon existence locked out of their account, users are forced to validate their identity -- a process that, while designed to dissuade nefarious actors, is as well troublesome for legitimate users.
"Business relationship lockout is, from a user perspective, a jarring and in-your-confront experience," said Allan Foster, chief evangelist at ForgeRock.
Merely the experience is integral to mitigate adventure, said Casey Ellis, CTO and founder of Bugcrowd.
"While inconvenient for legitimate users, it is non too inconvenient -- and information technology tin deter attackers," Ellis said. "It is a resilient and battle-tested reset strategy that is highly available for multiple use cases."
Why enterprises need account lockout policies
Account lockout policies aim to foreclose credential theft, credential stuffing and brute-force methods of guessing username and countersign combinations, thus preventing user account compromise and network intrusion.
This is an important aspect of not only securing enterprise systems, but as well securing users' personal accounts and data. Companies must determine confidently whether users trying to cosign are really who they say they are, or they risk falling victim to assail.
The default approach to this is to make it harder for potential attackers to compromise accounts. There are two main techniques used to practise this, Foster said. One manner is to irksome down the authentication wheel by making users expect longer and longer every time there is an unsuccessful login effort, he said.
The other technique is anomaly detection. "Account providers can close down the account when anomalous behavior is detected until they can connect with the original owner to confirm their identity for hallmark," Foster explained.
Account lockout policy features
The business relationship lockout policy is made upward of iii cardinal security settings: business relationship lockout duration, account lockout threshold and reset account lockout counter after. These policy settings help prevent attackers from guessing users' passwords. In addition, they decrease the likelihood of successful attacks on an system'southward network.
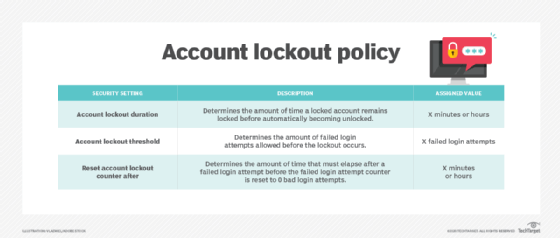
Enterprises should consider a combination of these three when edifice an account lockout policy.
Bugcrowd'due south Ellis recommended Apple'due south iPhone countersign lockout policy features. "If you forget or don't properly enter your password a certain number of times, you will be unable to try logging back in to the device for a short fourth dimension," he said. "Subsequent attempts extend the lockout flow. This can prove that either the individual entering the password is a forgetful user or an unauthorized individual attempting to obtain illegitimate access."
How to create account lockout policies
Setting business relationship lockout policies -- including lockout duration and thresholds -- is what Ellis called a "dark art."
There are many factors to consider when determining account lockout policy security setting values. Only, because every enterprise is different, information technology is difficult to recommend standard values for the 3 security settings without calculating the organization's risk profile kickoff. Policymakers should account for any regulatory requirements and arrange values accordingly. The capabilities of computing resources, equally well equally employee productivity, should also be accounted for.
Information technology is also critical to weigh exposure risks set by the security group, ForgeRock'south Foster said. "Accounts with different capabilities have different levels of risk, both to the user and to the organization in the event of a compromise," he said. "Any account where the damage that can be caused is loftier or is higher than normal requires a higher level of protection."
If a privileged business relationship shows any indication of assail, the immediate response should be to assume it is an set on and to lock downwards the account. Administrators may want to implement unique settings for privileged accounts, such equally a longer business relationship lockout duration and lower account lockout threshold.
While this seems similar a commonsense best do, it's important to consider the nuance of privileged accounts, Foster said. For example, some privileged accounts may be responsible for planning a response to a security event. "You don't want the reaction to the threat to also compromise your ability to answer to that threat," he added.
Analyzing these factors and hypotheticals is critical to successfully creating an account lockout policy that ensures security needs and UX needs are both met.
Limitations of account lockout policies
An account lockout policy alone is not a cybersecurity silver bullet. Enabling multifactor hallmark (MFA) and unmarried sign-on (SSO) are critical measures that should also exist incorporated into enterprise identity and admission direction programs, said Anurag Kahol, CTO and co-founder of Bitglass.
"MFA confirms user identity and investigates suspicious logins, while SSO helps organizations directly manage access to sensitive information by blocking or providing various levels of access to data and applications based on user identity and context," Kahol said.
Managing identities and access privileges has go even more demanding tasks as many organizations transition to remote work. Implementing the right policies and settings can empower administrators to manage and secure every account.
This was last published in September 2020
Dig Deeper on Identity and admission direction
-

Learn to adjust the AdminCount attribute in protected accounts
-

privileged access management (PAM)
-
![]()
Russia using Kubernetes cluster for animate being-force attacks
-
![]()
10 RDP security best practices to prevent cyberattacks
Source: https://www.techtarget.com/searchsecurity/answer/Account-lockout-policy-Addressing-too-many-failed-login-attempts






0 Response to "Locked Out After Third Attempt"
Enregistrer un commentaire